Securing Your Cheap Python Hosting Server: Best Practices

Introduction:
In an era where online threats are becoming increasingly sophisticated, the importance of
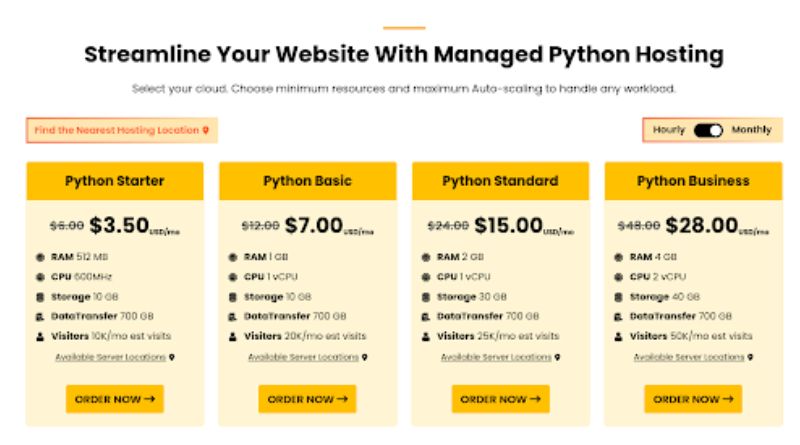
securing your Cheap Python hosting server cannot be overstated. As Python continues to be a preferred choice for web development, ensuring the robustness of your server’s security is paramount. In this extensive guide, we will explore a comprehensive set of best practices to fortify your Cheap Python hosting server. From fundamental server configurations to advanced application-level security, we’ve got you covered.
What is a Python Hosting Server
A Cheap Python hosting server refers to a server or a hosting environment specifically configured to run Python-based applications and websites. Python is a versatile programming language widely used for web development, data science, artificial intelligence, and various other applications. When you have a Python-based project, such as a web application or a data processing service, you need a server that can execute Python code and handle the associated dependencies.
Key components and considerations for a Python hosting server include:
- Web Server:
The server needs to have a web server installed, such as Apache, Nginx, or Gunicorn, to handle incoming HTTP requests and serve web pages or APIs.
- Python Interpreter:
The server must have a Python interpreter installed. Depending on the application’s requirements, you might use different versions of Python. Common choices include Python 2. x or Python 3. x.
- Dependencies and Libraries:
Ensure that the necessary Python libraries and dependencies for your application are installed on the server. This may include frameworks like Django or Flask, database connectors, and other third-party packages.
- Database Support:
If your Python application uses a database, the hosting server should support the chosen database system (e.g., MySQL, PostgreSQL, MongoDB).
- Operating System:
Python can run on various operating systems, including Linux, Windows, and macOS. Linux is a popular choice for hosting Python applications due to its stability and performance.
- Security Measures:
Implement security best practices, such as regular updates, firewalls, secure authentication, and encryption (SSL/TLS) to protect both the server and the data being transmitted.
- Scalability:
Depending on the anticipated traffic and workload, the hosting server should be scalable to accommodate increased demand. This may involve load balancing, clustering, or cloud-based solutions.
Popular hosting options for Python applications include traditional web hosting providers, cloud platforms like AWS (Amazon Web Services), Google Cloud Platform (GCP), or Microsoft Azure, as well as specialized Python hosting services.
In summary, a Python hosting server is a server environment optimized for running Python applications, providing the necessary infrastructure and support to ensure the smooth execution and delivery of Python-based services.
Securing Your Cheap Python Hosting Server
- Regular Software Updates:
Keep your server’s software stack up-to-date by regularly applying security patches. This includes updating the operating system, Python interpreter, and all relevant libraries. Utilize package managers like `apt` or `yum` to streamline the update process and stay vigilant about emerging vulnerabilities.
- Robust authentication Mechanisms:
Implementing strong authentication practices is crucial for server security. Use complex, unique passwords and consider adopting SSH key-based authentication for an additional layer of protection. It’s advisable to disable direct root login and instead create a dedicated user account with administrative privileges.
- Firewall Fortification:
Configure firewalls to allow only essential traffic. Leverage tools such as `ufw` or `iptables` to regulate incoming and outgoing connections. Minimize open ports and expose only the services essential for your application, reducing the attack surface.
- Backups as a Safety Net:
Frequent backups are your safety net in the event of data loss or a security incident. Automate the backup process and store backup copies in a secure offsite location. Regularly test the restoration process to ensure quick recovery in case of emergencies.
- SSL/TLS Encryption:
Enable SSL/TLS encryption to secure data during transit. Acquire SSL certificates from reputable certificate authorities to establish a trust layer for your domain.
- Two-Factor Authentication (2FA):
Implement 2FA for both server access and application logins. This additional layer of security, using tools like Google Authenticator or Authy, fortifies user authentication and minimizes the risk of unauthorized access.
- Monitoring and Logging:
Deploy monitoring tools to keep a constant watch on server performance and identify anomalies. Implement robust log management systems to collect and analyze logs, aiding in the detection and response to potential security incidents.
- Disable Unnecessary Services:
Trim down your server’s attack surface by disabling any unnecessary services or applications. Each active service is a potential vulnerability, so only enable what is essential for your application to function optimally.
- File Permissions Vigilance:
Carefully manage file and directory permissions to restrict access to sensitive areas. Limiting access to critical system files ensures that only authorized users can modify or access them, minimizing the risk of unauthorized manipulation.
- Application-Level Security Best Practices: Input Validation: Thoroughly validate and sanitize all user inputs to prevent common security vulnerabilities, including SQL injection and Cross-Site Scripting (XSS).
Web Application Firewall (WAF):
Incorporate a WAF to monitor and filter HTTP traffic, adding an extra layer of protection against various web-based attacks.
Secure Dependencies:
Regularly audit and update third-party dependencies. Tools like `pyup.io` can provide notifications about outdated or vulnerable packages in your Python projects.
Framework-Specific Considerations:
If using frameworks like Django or Flask, adhere to their specific security guidelines. Enable built-in security features in Django and implement Flask’s best practices for secure web development.
Conclusion:
Securing your Cheap Python hosting server is an ongoing commitment that demands a proactive and dynamic approach. By incorporating these best practices into your server management routine, you can significantly reduce the risk of security breaches and ensure the stability and integrity of your Python applications. Stay informed about emerging threats, regularly update your security measures, and fortify your hosting environment against the evolving landscape of cybersecurity challenges. A well-secured server is the foundation for a resilient and trustworthy online presence.







